Keystore is an authorization and issuance solution based on Invision Community 5 (IPS 5), covering a complete loop of "product management → card password issuance → authorization verification → order tracking". It will deeply integrate verification services with backend management, providing a plug and play commercial infrastructure.
-Composition
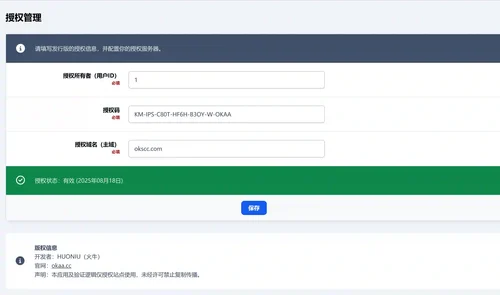
-Verification server: The built-in interface is responsible for authorizing decryption and integrity verification, time window verification, device/domain binding, and certificate signing.
-Client verification: The distribution has a built-in reinforcement verification process (HTTPS enforcement, domain whitelist, fixed UA, Base64URL packaging).
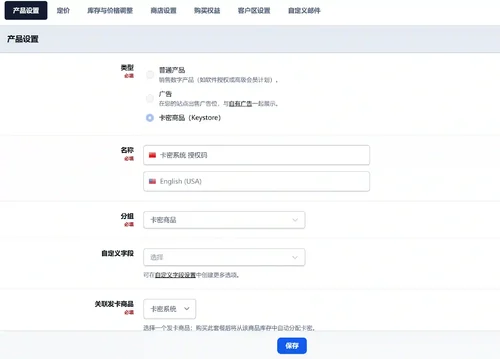
-Backend management: issuing products (without price fields), card vault, order flow and log auditing, focusing on issuing cards and authorization itself.
-Workflow
1) Create the issued product and configure the card password → 2) Deliver the card password to the end user → 3) Initiate encryption verification on the client side
→ 4) The server returns the authorization result and constraints (including signature/certificate) → 5) The backend can view the real-time order and authorization status.
##Key characteristics
-Secure Communication: AES-256-CBC Encryption+Base64URL Packaging+HMAC Integrity Verification
-Anti tampering: Fixed HTTPS authentication domain whitelist, built-in UA, disable plaintext rollback
-Authorization constraint: Supports domain/device binding and fingerprint verification to prevent dissemination and abuse
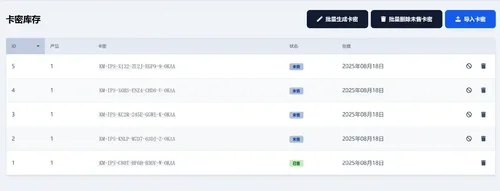
-Flexible card issuance: batch import/generation of card codes, inventory visibility and status management
-Order Tracking: Order List, Status Flow, and Audit Information
-Lightweight backend: integrated management of issued products, card codes, and orders (no product price field, more suitable for external store settlement)
-Compatibility: Compatible with IPS 5.0. x, following framework specifications, easy to switch on and off
##Applicable scenarios
-Forum/Community Business Plugin and Theme Distribution
-Theme and feature extensions for IPS 5, authorized by domain/site; Can limit the installation of terminals and the number of migrations.
-SaaS/Local Hybrid Authorization
-Online strong verification+short-term offline grace period; The combination of instance fingerprint, replay protection, and time window enhances reliability and anti abuse capabilities.
-Internal distribution and compliance audit of enterprises
-Unified issuance of cards for multiple sites/departments, binding domain names/devices, authorization can be migrated and revoked, and audit trails can be retained.
-Channel distribution and bulk issuance of cards
-Batch generation/import of card codes, channel identification and inventory/status management, supporting large-scale distribution and recycling.
-Regular trial and upgrade release
-Time limit card encryption, grayscale release, version upgrade pass; Automatically expires upon expiration, supports renewal/regularization.
-Connect with external stores/payment platforms
-Price and settlement are handled externally (such as Paddle/Stripe/domestic card issuing platforms, etc.), while Keystore focuses on authorization verification and card issuance closed-loop.
-Risk control and after-sales service
-Abnormal domain name/multiple migration warning; Blacklist/Revocation of Authorization; Orders, devices, and binding changes can be tracked throughout the entire chain.
##Why choose Keystore
-Stronger security baseline: time window verification, server authentication token (serverless), whitelist domain name
-Less configuration: Verify that the server address is built-in and reinforced, no need for users to configure it themselves
-Update process: Hand over the "price/amount" to an external store, with the backend only focusing on card issuance and authorization
##Safety Design Description (Brief)
-Encryption: AES-256-CBC, request/response symmetric encryption
-Packaging: timestamp+nonce+ciphertext → Base64URL, resistant to middleware rewriting
-Integrity: HMAC-SHA256 signature (including hour/date factor)+daily authentication with server _cert
-Transmission: Enforce HTTPS, fix domain whitelist, reject plaintext and untrusted addresses
##Installation and Getting Started (IPS 5)
1. Upload and install Keystore application in ACP application management
2. Open "Card Issued Products", "Card Password Management", and "Order Management" for basic configuration
3. Connect the client (plugin that requires authorization verification) to the authorization verification interface (encapsulated inside the plugin)
4. Import the card password and start selling it
Tip: The backend does not involve setting product prices; Please maintain the price in the external store/payment system.
##Frequently Asked Questions (FAQ)
-Q: Does it support offline?
A: Reasonable time windows and caching strategies can be configured to reduce the impact of short-term network fluctuations.
-Q: Can I customize the verification server?
A: Customization has been disabled for security and consistency, with built-in official verification address and reinforcement.
-Q: How to conduct secondary development?
A: Following the IPS application structure, the controller/model is clear and can be expanded as needed.
What's New in Version 5.0.8
Released
No changelog available for this version.
please support the developers. If you have any other questions
please leave a comment and let us know!




Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.